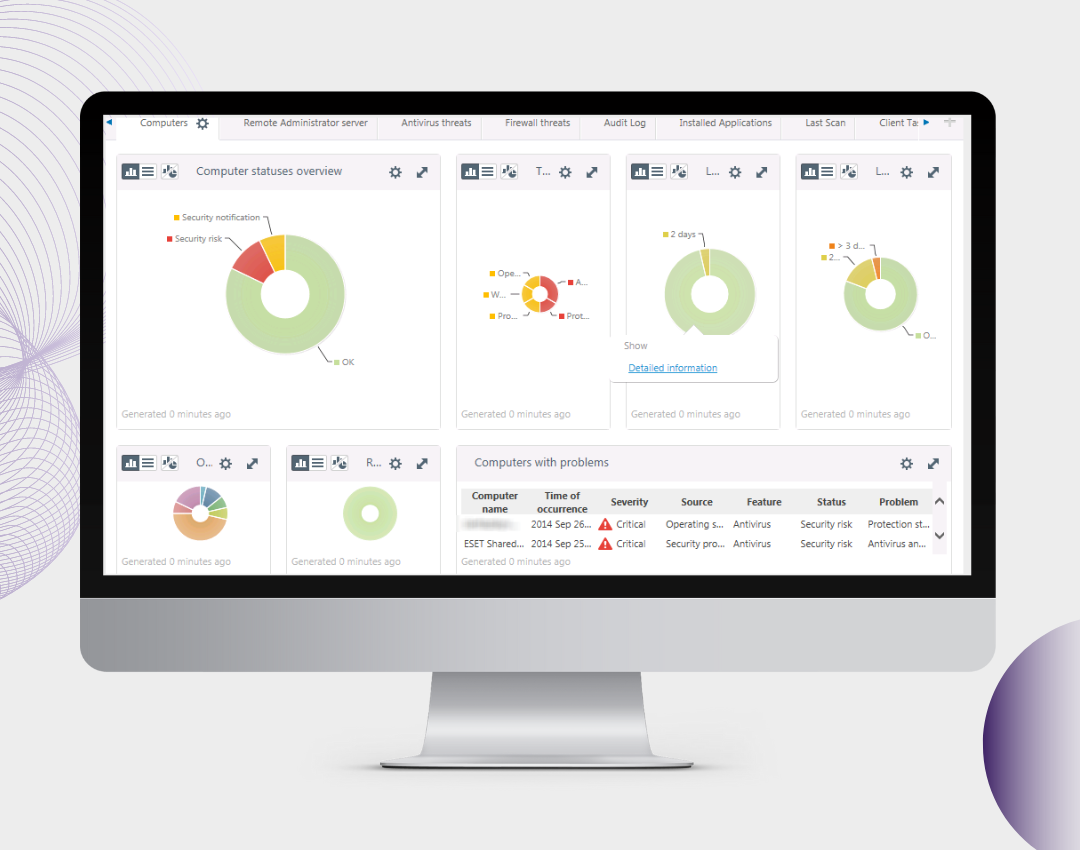
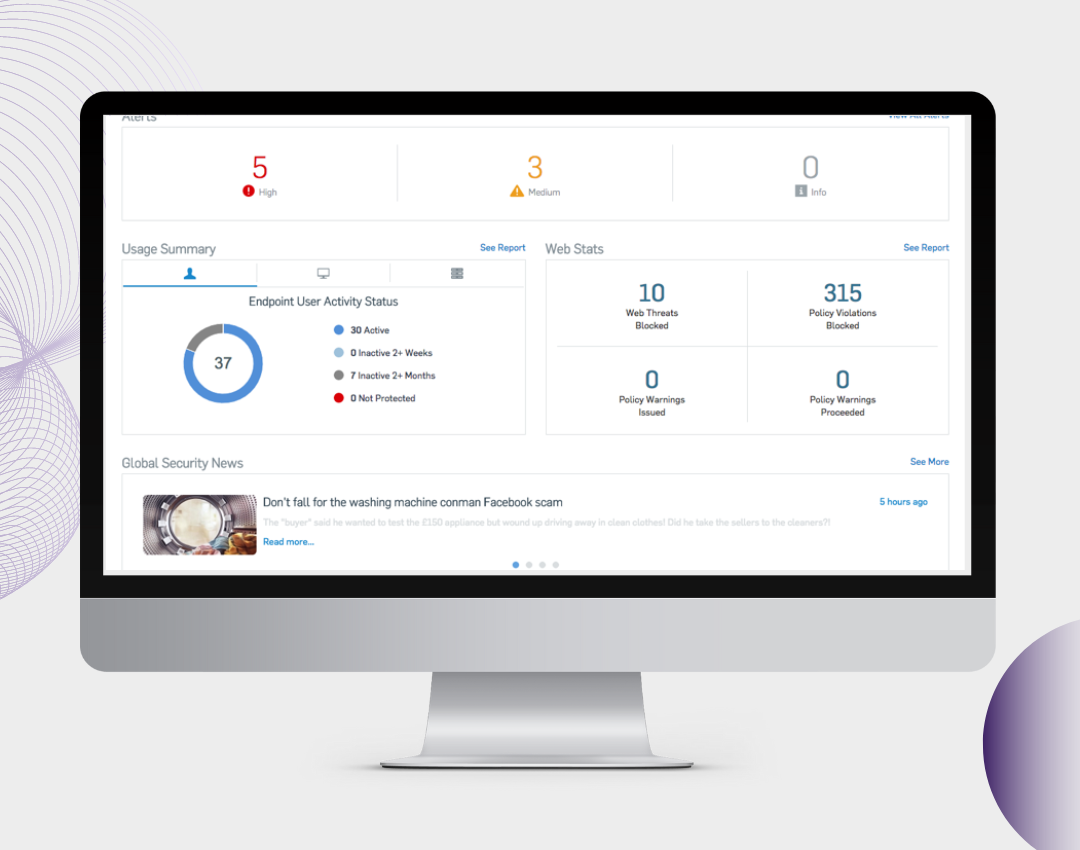
Endpoint Protection
What is an Endpoint Protection?
An Endpoint Protection Platform (EPP) is a security tool installed on business computers to stop online attacks, spot malicious activity, and offer quick detection and response to any actions from intruders. In other words, it is the practice of guarding against malicious actions and campaigns by endpoints or entry points of end-user devices like desktops, laptops, and mobile devices.
Endpoint Protection is capable of providing security such as anti-malware, web browser security, MDM, EDR, and DLP. It offers collaborative, layered security to detect and block most threats.
Endpoint Protection helps to
- Prevent ransomware
- Stop file-less attacks
- Avoid data breaches
- Identify & remove threats
How Does Endpoint Protection Work?
Endpoint Protection Platform (EPP) uses the latest and traditional technologies like Signature based analysis, Signatureless analysis, Behavior analysis, Machine learning, Artificial Intelligence & so on. If we install Endpoint Protection in a network, it will monitor all the files, processes, and systems from the server to client machines. And it will block any questionable or malicious activities that are getting triggered. It will prevent intruders and malicious activities using malware or other tools to access the network or systems. The basic steps of using Endpoint Protection are
-
1
Install Solution
-
2
Configure Policies
-
3
Monitor Notifications
-
4
Update Patches
Features
The Node IT
Explore our solutions, personal reflections and ideas that inspire action on the services you care about.
Contact us!
FAQ About Endpoint Protection
What is Endpoint Protection?
Endpoint Protection refers to security solutions installed on end-user devices such as desktops, laptops, and mobile devices to prevent online attacks, detect malicious activities, and provide rapid responses to intrusions. At The Node IT, we offer comprehensive Endpoint Protection services designed to safeguard your business’s digital assets. Our solutions include advanced, multi-layered defenses against diverse threats, ensuring top performance while preserving user productivity. We provide industry-leading solutions that address threats across the entire attack chain, offering the highest return on investment with easy deployment and management as single-agent solutions.
How does Endpoint Protection work?
Endpoint Protection operates by installing security software on devices such as computers, laptops, and mobile devices. This software serves to prevent online attacks, detect malicious activities, and provide rapid responses to intrusions. At The Node IT, our Endpoint Protection solutions are designed to safeguard your business’s digital assets by offering advanced, multi-layered defenses against diverse threats. Our approach ensures top performance while preserving user productivity, providing industry-leading solutions that address threats across the entire attack chain. This comprehensive protection offers a high return on investment with easy deployment and management as single-agent solutions.
What are the main features of Endpoint Protection?
At The Node IT, our Endpoint Protection solutions offer a comprehensive suite of features designed to safeguard your organization’s digital assets:
- Antivirus and Antimalware: Scans and eradicates malware that arrives on a system.
- Firewall and Intrusion Prevention: Blocks malware before it spreads to the machine and controls traffic.
- Application and Device Control: Controls file, registry, and device access and behavior with whitelisting and blacklisting.
- Exploit Prevention: Blocks memory-based zero-day exploits of vulnerabilities in popular software.
- Data Loss Prevention (DLP): Monitors and protects data at any stage, ensuring data in motion or at rest, whether on-premises or in cloud storage, is secure.
These integrated features collaborate to provide a robust, multi-layered defense against a wide array of cyber threats, ensuring the security and integrity of your organization’s IT infrastructure.
How can Endpoint Protection prevent ransomware attacks?
At The Node IT, our Endpoint Protection solutions are designed to prevent ransomware attacks through a multi-layered security approach:
- Advanced Malware Detection: Utilizing sophisticated algorithms to identify and block ransomware before it can execute.
- Exploit Prevention: Protecting against vulnerabilities that ransomware may exploit to infiltrate systems.
- Behavioral Analysis: Monitoring system activities to detect and halt suspicious behaviors indicative of ransomware.
- Data Encryption: Safeguarding sensitive information, making it inaccessible to unauthorized entities.
These integrated features ensure comprehensive protection against ransomware threats, maintaining the integrity and security of your organization’s data and systems.
How can I install and configure Endpoint Protection?
At The Node IT, we offer comprehensive Endpoint Protection solutions tailored to your organization’s needs. While our website does not provide specific installation and configuration instructions, our team is dedicated to assisting you through the process. To ensure optimal protection:
- Consult Our Experts: Reach out to our team for personalized guidance tailored to your organization’s unique requirements.
- Professional Installation: Our specialists can perform the installation, ensuring all security features are correctly implemented.
- Customized Configuration: We will configure the settings to align with your operational needs, maximizing security without compromising performance.
For detailed assistance, please contact us through our website. Our dedicated professionals are ready to help you establish a robust security framework.
What steps are involved in maintaining Endpoint Protection?
Regularly update endpoint protection software to patch vulnerabilities.
- Conduct routine scans to detect and eliminate threats.
- Monitor security alerts and respond to incidents promptly.
- Enforce strong access controls and authentication policies.
- Implement endpoint detection and response (EDR) solutions for real-time threat analysis.
- Educate employees on cybersecurity best practices to prevent phishing and malware attacks.
- Regularly back up critical data to mitigate risks of data loss.
- Configure firewalls and intrusion prevention systems for added security.
- Perform security audits to identify and address potential weaknesses.
- Ensure compliance with industry regulations and security standards.
How does Endpoint Protection improve network security?
Endpoint protection enhances network security by safeguarding devices from cyber threats.
- It prevents malware, ransomware, and unauthorized access, reducing the risk of data breaches.
- Real-time monitoring and threat detection help identify and neutralize threats before they spread.
- Advanced encryption ensures data security, even if a device is compromised.
- Centralized management allows IT teams to enforce security policies across all endpoints.
- Regular updates protect against emerging cyber threats.
By implementing endpoint protection, businesses can secure their network, maintain compliance, and ensure uninterrupted operations. Learn more at The Node IT.